Imagine being able to securely connect your business networks across different locations, without the hassle of complex setup and maintenance. With Azure VPN Gateway, you can now achieve just that. This powerful tool ensures secure networking by providing a seamless and encrypted connection between your on-premises network and virtual networks in Azure. Say goodbye to potential security vulnerabilities and hello to a more efficient and protected network infrastructure. Azure VPN Gateway is a game-changer for businesses looking to enhance their network security without compromising on performance and ease of use.
What is Azure VPN Gateway?
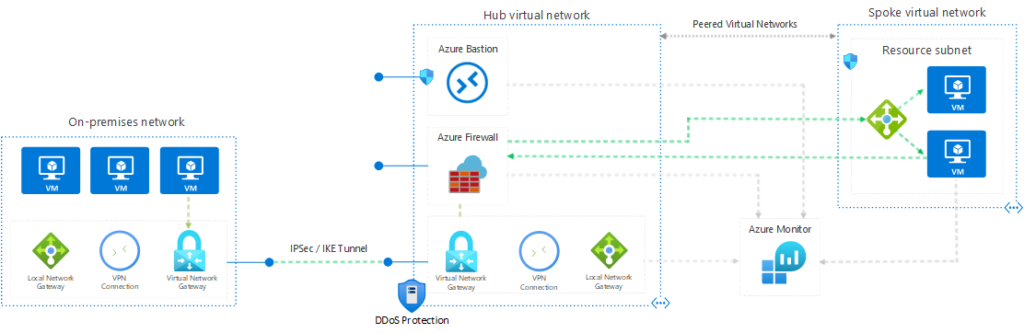
Overview
Azure VPN Gateway is a cloud-based virtual private network (VPN) service offered by Microsoft Azure. It allows you to securely connect your on-premises network to the Azure cloud environment, creating a secure and private connection for your data and resources.
Key Features
Azure VPN Gateway comes with several key features that make it a reliable and robust solution for secure networking:
-
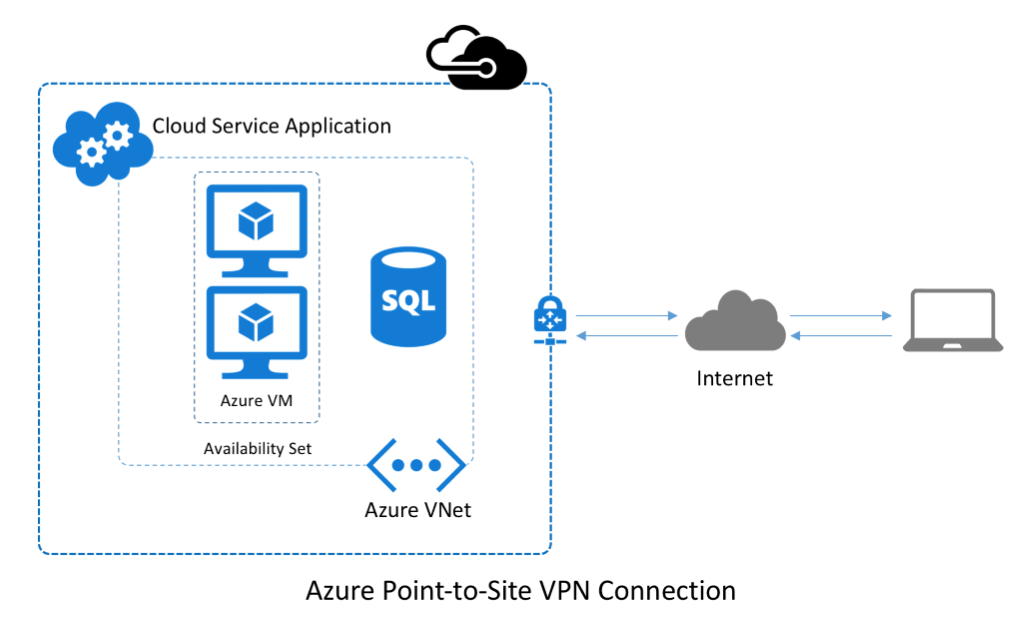
Point-to-Site (P2S) VPN: Allows individual users to securely access Azure resources from remote locations using an SSL-VPN connection.
-
Site-to-Site (S2S) VPN: Enables secure communication between your on-premises network and Azure virtual network, extending your on-premises infrastructure to Azure.
-
VNet-to-VNet VPN: Connects two Azure virtual networks, enabling secure communication and resource sharing between them.
-
Multi-Factor Authentication: Facilitates an additional layer of security by requiring multiple forms of authentication for user access to the Azure VPN Gateway.
-
Certificates: Provides the capability to use certificates for authentication and encryption, ensuring secure communication between your on-premises network and Azure.
-
Network Security Groups: Allows you to define granular network traffic rules to control inbound and outbound traffic to and from Azure VPN Gateway.
-
High Availability and Scalability: Offers options for configuring active-active or active-standby configurations for increased availability and the ability to scale the VPN Gateway up or down to match your network demands.
-
Monitoring and Diagnostics: Provides comprehensive monitoring capabilities through VPN Gateway diagnostics logs, Azure Monitor, metrics, and alerts, helping you monitor and troubleshoot any issues.
-
Integration with Azure Firewall: Enables seamless integration with Azure Firewall, combining the security benefits of both services to enhance your overall network security posture.
-
Optimizing Performance: Allows you to optimize the performance of your VPN Gateway by considering bandwidth requirements and selecting the appropriate Gateway SKU.
-
Connectivity with On-Premises Networks: Facilitates integration with ExpressRoute, offers various traffic routing options, and enables integration with Network Traffic Manager for efficient and reliable connectivity between your on-premises network and Azure.
-
Best Practices: Provides guidance and best practices for configuring and securing your Azure VPN Gateway, ensuring optimal performance and security of your network.
With these key features, Azure VPN Gateway offers a robust and secure solution for connecting your on-premises network to the Azure cloud environment.
Setting Up an Azure VPN Gateway
Setting up an Azure VPN Gateway involves several steps that need to be followed in order to establish a secure connection between your on-premises network and the Azure environment.
Prerequisites
Before setting up an Azure VPN Gateway, you need to have the following prerequisites in place:
-
An Azure subscription – You need an active subscription to Azure in order to create and configure a VPN Gateway.
-
A virtual network (VNet) – You should have a virtual network set up in Azure where the VPN Gateway will be deployed.
-
On-premises network – You need to have an on-premises network with an internet connection that will serve as one end of the VPN connection.
-
Public IP address – You need a public IP address for the VPN Gateway, which will be used to establish the VPN connection.
Creating a Virtual Network
To set up an Azure VPN Gateway, you first need to create a virtual network in Azure. This virtual network acts as a container for your Azure resources and provides the network infrastructure for the VPN Gateway.
To create a virtual network, follow these steps:
- Log in to the Azure portal.
- Click on “Create a resource” and search for “Virtual network”.
- Select “Virtual network” from the search results and click on “Create”.
- Provide the required details like the name, address space, and subnet configuration for the virtual network.
- Click on “Create” to create the virtual network.
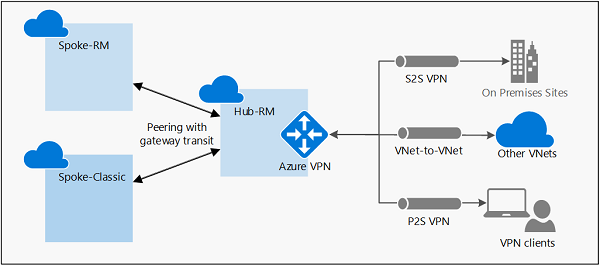
Deploying the VPN Gateway
Once you have created the virtual network, the next step is to deploy the VPN Gateway within the virtual network. This will establish the secure connection between your on-premises network and Azure.
Follow these steps to deploy the VPN Gateway:
- Navigate to the virtual network created in the previous step.
- Click on “Add” to add a new resource to the virtual network.
- Search for “Virtual network gateway” and select it from the search results.
- Provide the required details for the VPN Gateway, such as the name, VPN type, SKU, and public IP address.
- Review the settings and click on “Create” to deploy the VPN Gateway.
Configuring Connections
After deploying the VPN Gateway, you need to configure the connections to establish the secure communication between your on-premises network and Azure.
To configure connections, follow these steps:
- Navigate to the virtual network gateway created in the previous step.
- Click on “Connections” and then click on “Add”.
- Provide the required details, such as the name, connection type (Site-to-Site or Point-to-Site), and the local network gateway (your on-premises network).
- Configure any additional settings, such as encryption and authentication methods.
- Click on “OK” to establish the connection.
Troubleshooting
If you encounter any issues while setting up or configuring your Azure VPN Gateway, Azure provides a set of troubleshooting tools and resources to help you identify and resolve problems.
Some common troubleshooting steps include:
- Checking the VPN Gateway diagnostics logs for any errors or warnings.
- Reviewing the Azure Monitor metrics and alerts to identify any issues with the VPN Gateway.
- Verifying the network security groups and rules to ensure that the required ports are open for VPN traffic.
- Double-checking the configuration settings of your VPN Gateway and the on-premises network gateway to ensure they match.
If the issue persists, it is recommended to seek support from Azure technical support or consult the Azure documentation for further troubleshooting steps.
By following these steps and utilizing the available troubleshooting resources, you can effectively set up and configure your Azure VPN Gateway for secure networking.
Types of VPN Connections
Azure VPN Gateway supports different types of VPN connections, each serving specific networking requirements. Understanding these types will help you choose the appropriate connection for your needs.
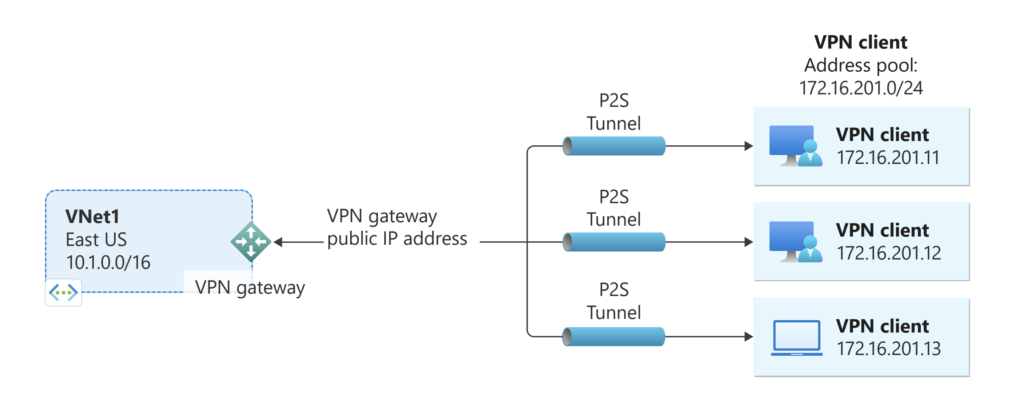
Point-to-Site (P2S) VPN
Point-to-Site VPN enables individual users to securely connect to Azure resources from remote locations using an SSL-VPN connection. This type of connection is ideal for remote workers or employees who require secure access to the Azure cloud environment.
To set up a Point-to-Site VPN, users need to install a client VPN software on their devices and authenticate using their Azure Active Directory credentials.
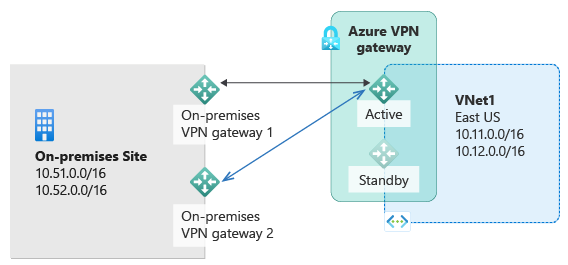
Site-to-Site (S2S) VPN
Site-to-Site VPN allows secure communication between your on-premises network and the Azure virtual network. It extends your on-premises infrastructure to Azure, enabling seamless communication and resource sharing.
To establish a Site-to-Site VPN connection, you need to configure a local network gateway in Azure that represents your on-premises network. This connection can be established over the internet using VPN protocols like IPsec.
VNet-to-VNet VPN
VNet-to-VNet VPN connects two Azure virtual networks, enabling secure communication and resource sharing between them. This type of connection is useful when you have multiple virtual networks in Azure and need to establish connectivity between them.
To set up a VNet-to-VNet VPN, you need to configure a connection between the virtual network gateways of the two virtual networks. This connection can be established over the internet using VPN protocols like IPsec.
Understanding the different types of VPN connections offered by Azure VPN Gateway will help you select the most appropriate connection type for your networking requirements.
Securing the Azure VPN Gateway
Securing your Azure VPN Gateway is crucial to protect your network and data. Azure VPN Gateway offers several security features to enhance the overall security posture of your network.
Multi-Factor Authentication
Enabling Multi-Factor Authentication (MFA) adds an extra layer of security to your Azure VPN Gateway. With MFA, users are required to provide multiple forms of authentication, such as a password and a generated one-time passcode, to access the VPN Gateway. This helps prevent unauthorized access and enhances the overall security of your network.
Certificates
Using certificates for authentication and encryption is another important security measure for Azure VPN Gateway. By configuring certificate-based authentication, you ensure that only devices with authorized certificates can establish a connection to the VPN Gateway. This adds an additional layer of security and prevents unauthorized access to your network.
Network Security Groups
Network Security Groups (NSGs) allow you to define granular network traffic rules to control inbound and outbound traffic to and from Azure VPN Gateway. By configuring NSGs, you can restrict access to specific IP addresses or ports, reducing the attack surface and protecting your network from unauthorized access.
By implementing these security measures, you can enhance the security of your Azure VPN Gateway and protect your network and data from potential threats.
High Availability and Scalability
Azure VPN Gateway offers options for high availability and scalability, ensuring that your network connectivity remains reliable and can handle increased demands.
Active-Active Configuration
In an Active-Active configuration, you can deploy multiple VPN Gateways in different Azure regions, providing redundancy and high availability. This configuration enables simultaneous connections to different VPN Gateways, improving overall network resilience and ensuring uninterrupted connectivity.
Active-Standby Configuration
In an Active-Standby configuration, you have a primary VPN Gateway and a secondary standby VPN Gateway. The secondary VPN Gateway remains inactive until the primary Gateway fails, at which point the standby Gateway takes over. This configuration provides failover capabilities and ensures continuous availability of your network connection.
Scaling up or down
Azure VPN Gateway allows you to scale up or down based on your network needs. You can change the Gateway SKU to increase or decrease the VPN Gateway’s capacity, adjusting it according to your network traffic requirements. This scalability feature ensures that your VPN Gateway can handle varying network demands and provides optimal performance.
By leveraging these high availability and scalability options, you can ensure continuous connectivity and adaptability to changing network requirements.
Monitoring and Diagnostics
Monitoring and diagnosing the performance and health of your Azure VPN Gateway is crucial for maintaining the integrity of your network connection.
VPN Gateway Diagnostics Logs
Azure VPN Gateway provides comprehensive diagnostics logs that capture detailed information about the VPN Gateway’s performance. These logs help you identify any issues or anomalies and facilitate troubleshooting. By analyzing the diagnostics logs, you can gain insights into the performance of your VPN Gateway and address any potential problems proactively.
Azure Monitor
Azure Monitor is a monitoring service that provides a centralized platform for monitoring your Azure resources, including the Azure VPN Gateway. It offers various monitoring capabilities, such as alerts, dashboards, and log analytics, allowing you to monitor and proactively manage the performance and health of your VPN Gateway.
Metrics and Alerts
Azure VPN Gateway provides a set of metrics and alerts that give insight into the health and performance of your VPN Gateway. You can configure alerts based on specific metrics, such as VPN tunnel status, data transfer rates, or VPN Gateway uptime. By setting up alerts, you can be notified of any crucial events or performance degradations, allowing you to take timely action.
By utilizing VPN Gateway diagnostics logs, Azure Monitor, and metrics and alerts, you can proactively monitor your Azure VPN Gateway and ensure uninterrupted network connectivity.
Integration with Azure Firewall
Integrating Azure VPN Gateway with Azure Firewall allows you to combine the security benefits of both services, enhancing your overall network security posture.
Combining Azure VPN Gateway and Azure Firewall
Azure VPN Gateway provides secure connectivity to your on-premises network and Azure resources. It encrypts the network traffic and establishes a secure tunnel between your on-premises network and Azure. On the other hand, Azure Firewall is a cloud-native network security service that provides advanced threat protection and network traffic filtering.
By integrating Azure VPN Gateway and Azure Firewall, you can enforce network security policies and filter network traffic passing through the VPN Gateway. This combination helps in protecting your network resources from unauthorized access and potential threats.
Configuration Steps
To integrate Azure VPN Gateway and Azure Firewall, follow these steps:
- Set up Azure VPN Gateway and Azure Firewall separately according to their respective configuration requirements.
- Configure the network rules in Azure Firewall to allow inbound and outbound traffic for your VPN Gateway.
- Configure the VPN Gateway to use Azure Firewall as the next hop for network traffic filtering.
- Enable forced tunneling if necessary, to ensure that all network traffic from the VPN Gateway is routed through Azure Firewall.
By following these configuration steps, you can seamlessly integrate Azure VPN Gateway with Azure Firewall and enhance your network security.
Optimizing Performance
Optimizing the performance of your Azure VPN Gateway is essential to ensure fast and reliable network connectivity between your on-premises network and Azure.
Bandwidth Considerations
Consider the bandwidth requirements of your network when setting up and configuring your Azure VPN Gateway. High bandwidth applications like video conferencing or large file transfers may require higher capacity gateways to ensure optimal performance. It is important to select a Gateway SKU that matches the bandwidth requirements of your network traffic.
Selecting the appropriate Gateway SKU
Azure VPN Gateway offers different Gateway SKUs with varying performance capacities. When selecting a Gateway SKU, consider factors such as the expected network traffic volume, the number of connected devices, and the desired level of performance. Choosing the appropriate Gateway SKU ensures that your VPN Gateway can handle the expected workload and provides optimized performance.
By considering bandwidth requirements and selecting the appropriate Gateway SKU, you can optimize the performance of your Azure VPN Gateway and ensure seamless network connectivity.
Connectivity with On-Premises Networks
Azure VPN Gateway offers various connectivity options to establish secure connections between your on-premises network and Azure.
ExpressRoute Integration
ExpressRoute is a dedicated private network connection between your on-premises network and Azure. By integrating Azure VPN Gateway with ExpressRoute, you can establish a hybrid network architecture that combines the benefits of both services. This integration allows you to route your network traffic through ExpressRoute for more reliable and predictable connectivity.
Traffic Routing Options
Azure VPN Gateway provides different traffic routing options to optimize connectivity between your on-premises network and Azure. You can configure the routing to use either BGP (Border Gateway Protocol) or static routing, depending on your network requirements and preferences. BGP offers dynamic routing capabilities and is suitable for large-scale networks, while static routing provides simplicity and ease of configuration.
Network Traffic Manager Integration
Integrating Azure VPN Gateway with Network Traffic Manager allows you to distribute incoming traffic between multiple VPN Gateway instances, ensuring load balancing and optimal network performance. This integration helps in achieving high availability and scalability for your network connection.
By leveraging ExpressRoute integration, traffic routing options, and Network Traffic Manager integration, you can establish a secure and reliable connection between your on-premises network and Azure.
Best Practices for Azure VPN Gateway
To ensure optimal performance, security, and reliability of your Azure VPN Gateway, it is important to follow best practices during configuration and deployment.
Understanding Network Latency
Consider network latency when planning and configuring your Azure VPN Gateway. Network latency is the delay in communication between two points on a network and can impact the performance of your VPN connection. Minimizing network latency by selecting the appropriate Gateway SKU, optimizing your network infrastructure, and choosing the right Azure region can greatly enhance the performance of your VPN Gateway.
Configuring Security Baselines
Implementing security baselines ensures that your Azure VPN Gateway is configured securely. This involves adhering to security best practices, such as enabling Multi-Factor Authentication (MFA), using certificates for authentication and encryption, and configuring network security groups (NSGs) to control network traffic.
Regularly reviewing and updating security baselines based on industry standards and guidelines helps protect your network resources from potential threats and vulnerabilities.
By understanding network latency and configuring security baselines, you can enhance the performance and security of your Azure VPN Gateway.
In conclusion, Azure VPN Gateway provides a comprehensive and secure solution for connecting your on-premises network to the Azure cloud environment. With key features like Point-to-Site and Site-to-Site VPN, multi-factor authentication, high availability and scalability options, and integration with Azure Firewall, Azure VPN Gateway ensures secure networking and reliable connectivity. By following best practices and optimizing performance, you can effectively leverage Azure VPN Gateway for your networking requirements.