Are you concerned about the security of your cloud assets? Look no further than Azure Security and Compliance. This comprehensive solution offers robust protection for your valuable data and resources, ensuring that you can rest easy knowing your assets are safeguarded. With an array of advanced features, Azure Security and Compliance is your trusted partner in defending against potential threats and maintaining regulatory compliance. Get ready to take your cloud security to the next level with Azure Security and Compliance.
Securing Your Cloud Environment
When it comes to securing your cloud environment, there are several important areas to focus on: implementing strong access controls, enforcing network security, and encrypting data at rest and in transit. By following these best practices, you can ensure that your cloud assets are protected from unauthorized access and potential threats.
Implementing strong access controls
One of the key components to securing your cloud environment is implementing strong access controls. This involves managing user identities and permissions to ensure that only authorized users have access to your resources. Azure provides several tools and services to help you achieve this, such as Azure Active Directory (AAD), Role-Based Access Control (RBAC), and Multi-Factor Authentication (MFA).
AAD is a comprehensive identity and access management solution in Azure that provides a centralized directory for user sign-in and access management. RBAC allows you to control access to your Azure resources by assigning users to roles with specific permissions. MFA adds an extra layer of security by requiring users to verify their identity using multiple factors, such as a password and a code sent to their phone.
Enforcing network security
Another important aspect of securing your cloud environment is enforcing network security. This involves protecting your cloud resources from unauthorized network access and potential attacks. Azure provides several tools and services to help you accomplish this, such as Azure ExpressRoute, Virtual Private Network (VPN), and Azure Firewall.
Azure ExpressRoute allows you to establish a dedicated private connection between your on-premises network and Azure, bypassing the public internet. This not only provides a more secure and reliable connection, but also ensures that your data remains within your private network. VPN, on the other hand, allows you to securely connect to your Azure resources over the internet using encrypted tunnels. Azure Firewall is a managed firewall service that provides built-in protection for your Azure resources, including application and network-level filtering.
Encrypting data at rest and in transit
Data encryption is a critical component of securing your cloud environment. It ensures that even if your data falls into the wrong hands, it remains secure and unreadable. Azure provides several tools and services to help you encrypt your data at rest and in transit, such as data encryption, Azure Key Vault, and Data Loss Prevention (DLP).
Data encryption involves transforming your data into an unreadable format using an encryption algorithm. Azure offers server-side encryption for storing your data at rest, ensuring that it remains encrypted even when it’s not being actively used. Azure Key Vault is a secure key management service that allows you to safeguard and control cryptographic keys and secrets used by your applications. DLP helps you identify and protect sensitive information within your organization, preventing it from being leaked or compromised.
Identity and Access Management
Identity and access management (IAM) is a crucial aspect of maintaining the security of your cloud environment. Azure provides several tools and services to help you manage identities and control access to your resources effectively.
Azure Active Directory (AAD)
Azure Active Directory (AAD) is a comprehensive identity and access management solution that provides a centralized directory for user sign-in and access management. It allows you to manage user identities and control access to your Azure resources. AAD provides features such as single sign-on (SSO), multi-factor authentication (MFA), and device management. With AAD, you can ensure that only authorized users can access your resources and enforce strong security controls.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a powerful tool in Azure that allows you to manage access to your Azure resources by assigning users to roles with specific permissions. RBAC provides a granular level of control over who can perform specific actions on your resources. By assigning users to appropriate roles, you can ensure that they have the necessary access to perform their tasks without granting unnecessary privileges.
Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) adds an extra layer of security to your Azure environment by requiring users to verify their identity using multiple factors. This can include something they know (such as a password), something they have (such as a code sent to their phone), or something they are (such as a fingerprint). By enabling MFA, you can significantly reduce the risk of unauthorized access to your resources, even if a user’s password is compromised.
Network Security
Network security is a crucial aspect of securing your cloud environment. Azure provides several tools and services to help you enforce network security and protect your resources from unauthorized access.
Azure ExpressRoute
Azure ExpressRoute allows you to establish a dedicated private connection between your on-premises network and Azure. This private connection bypasses the public internet, providing a more secure and reliable connection. With ExpressRoute, you can ensure that your data remains within your private network and is not exposed to potential threats on the internet.
Virtual Private Network (VPN)
Virtual Private Network (VPN) allows you to securely connect to your Azure resources over the internet using encrypted tunnels. VPN provides a secure and encrypted connection between your on-premises network and Azure, ensuring that your data is protected from unauthorized access. By using VPN, you can securely extend your on-premises network to Azure and access your resources as if they were on the same network.
Azure Firewall
Azure Firewall is a managed firewall service that provides built-in protection for your Azure resources. It allows you to create and enforce network-level and application-level filtering rules to control inbound and outbound traffic. With Azure Firewall, you can monitor and control network traffic to and from your Azure resources, protecting them from potential threats and attacks.
Data Protection
Data protection is a critical aspect of securing your cloud environment. Azure offers several tools and services to help you encrypt your data, manage cryptographic keys, and prevent data loss.
Data encryption
Data encryption is a fundamental aspect of data protection. Azure provides server-side encryption for storing your data at rest, ensuring that it remains encrypted even when it’s not being actively used. By encrypting your data, you can protect it from unauthorized access and ensure its confidentiality.
Azure Key Vault
Azure Key Vault is a secure key management service that allows you to safeguard and control cryptographic keys and secrets used by your applications. It provides a centralized location to store and manage keys, ensuring that they are protected from unauthorized access. By using Azure Key Vault, you can ensure that your cryptographic keys are stored and managed securely, reducing the risk of key exposure.
Data loss prevention (DLP)
Data loss prevention (DLP) is a set of policies and technologies that help you identify and protect sensitive information within your organization. Azure offers several DLP capabilities to help you prevent the accidental or intentional disclosure of sensitive data. By using DLP, you can classify and protect sensitive information, monitor its usage, and prevent it from being leaked or compromised.
Threat Detection and Response
Threat detection and response are crucial in ensuring the security of your cloud environment. Azure provides several tools and services to help you detect and respond to potential threats and attacks.
Azure Security Center
Azure Security Center is a unified security management and monitoring service that helps you prevent, detect, and respond to security threats in your Azure environment. It provides a centralized dashboard for managing security policies, assessing the security of your resources, and monitoring for potential threats. By using Azure Security Center, you can gain insights into the security posture of your environment and take proactive measures to protect your resources.
Azure Advanced Threat Protection (ATP)
Azure Advanced Threat Protection (ATP) is a cloud-based solution that helps you identify, detect, and investigate advanced threats in your environment. It uses machine learning and behavioral analytics to analyze user behavior and network activities, identifying suspicious activities and potential threats. By using ATP, you can enhance your threat detection capabilities and respond to potential attacks more effectively.
Azure Sentinel
Azure Sentinel is a cloud-native security information and event management (SIEM) service that provides intelligent security analytics and threat intelligence across your entire environment. It collects security-related data from various sources, analyzes it using advanced machine learning algorithms, and provides actionable insights and alerts. With Azure Sentinel, you can detect and respond to security incidents more efficiently and effectively.
Governance and Compliance
Governance and compliance are essential aspects of maintaining the security and integrity of your cloud environment. Azure provides several tools and services to help you enforce governance policies, manage resources, and ensure compliance with industry and regulatory requirements.
Azure Policy
Azure Policy is a governance service that helps you enforce organizational standards and compliance by defining and applying policies for your Azure resources. With Azure Policy, you can enforce rules and best practices across your organization, ensuring that resources are deployed and managed according to your requirements. It allows you to define policies that govern various aspects of your resources, such as resource type, location, and tagging, among others.
Azure Resource Manager (ARM)
Azure Resource Manager (ARM) is the deployment and management service for Azure resources. It provides a consistent management layer for organizing, deploying, and managing resources in your Azure environment. With ARM, you can group resources into resource groups, manage their lifecycle, and enforce access controls and policies. By using ARM, you can ensure that your resources are organized, managed, and secured effectively.
Security baselines
Security baselines are predefined sets of security configurations and best practices that help you secure your Azure environment. Azure provides several security baselines that you can apply to your resources, such as Azure CIS Foundations Benchmark, Azure Security Benchmark, and Azure AD Security Baseline, among others. By applying these security baselines, you can ensure that your resources are configured securely and compliant with industry and regulatory requirements.
Secure DevOps Practices
Secure DevOps practices involve integrating security into the development lifecycle, following secure coding practices, and implementing continuous monitoring and testing. By following these practices, you can ensure that your cloud applications and services are developed and deployed securely.
Integrating security in the development lifecycle
Integrating security in the development lifecycle involves incorporating security considerations and practices into each stage of the development process. This includes requirements gathering, design, development, testing, and deployment. By integrating security early in the development lifecycle, you can identify and mitigate potential security risks before they become more significant and costly to address.
Secure coding practices
Secure coding practices involve following industry best practices and guidelines for writing secure code. This includes principles such as validating input, protecting against common vulnerabilities, sanitizing user input, and encrypting sensitive data. By following secure coding practices, you can reduce the risk of security vulnerabilities in your code and ensure that your applications are resistant to potential attacks.
Continuous monitoring and testing
Continuous monitoring and testing involve regularly monitoring and testing your cloud applications and services for potential security vulnerabilities and threats. This includes practices such as vulnerability scanning, penetration testing, and security incident response planning. By continuously monitoring and testing your applications, you can identify and address security issues proactively, ensuring that your cloud environment remains secure.
Security Monitoring and Incident Response
Security monitoring and incident response are critical aspects of maintaining the security of your cloud environment. Azure provides several tools and services to help you monitor and analyze security-related data and respond to potential security incidents.
Azure Monitor
Azure Monitor is a comprehensive monitoring service that helps you collect, analyze, and act on telemetry data from your Azure resources. It provides insights into the performance and availability of your resources, as well as the ability to set up alerts and notifications for potential security issues. By using Azure Monitor, you can gain visibility into the security posture of your environment and respond to potential threats more effectively.
Azure Log Analytics
Azure Log Analytics is a service that helps you collect, analyze, and visualize log data from various sources in your Azure environment. It allows you to collect and centralize log data, create custom queries and alerts, and gain insights into the health and performance of your resources. By using Azure Log Analytics, you can monitor security-related events and activities in your environment and detect potential security incidents.
Security incident response plan
A security incident response plan is a documented set of procedures and guidelines that define how your organization responds to potential security incidents. It includes steps for detecting, assessing, containing, and recovering from security incidents. By having a well-defined incident response plan in place, you can respond to security incidents effectively and minimize the impact on your cloud environment.
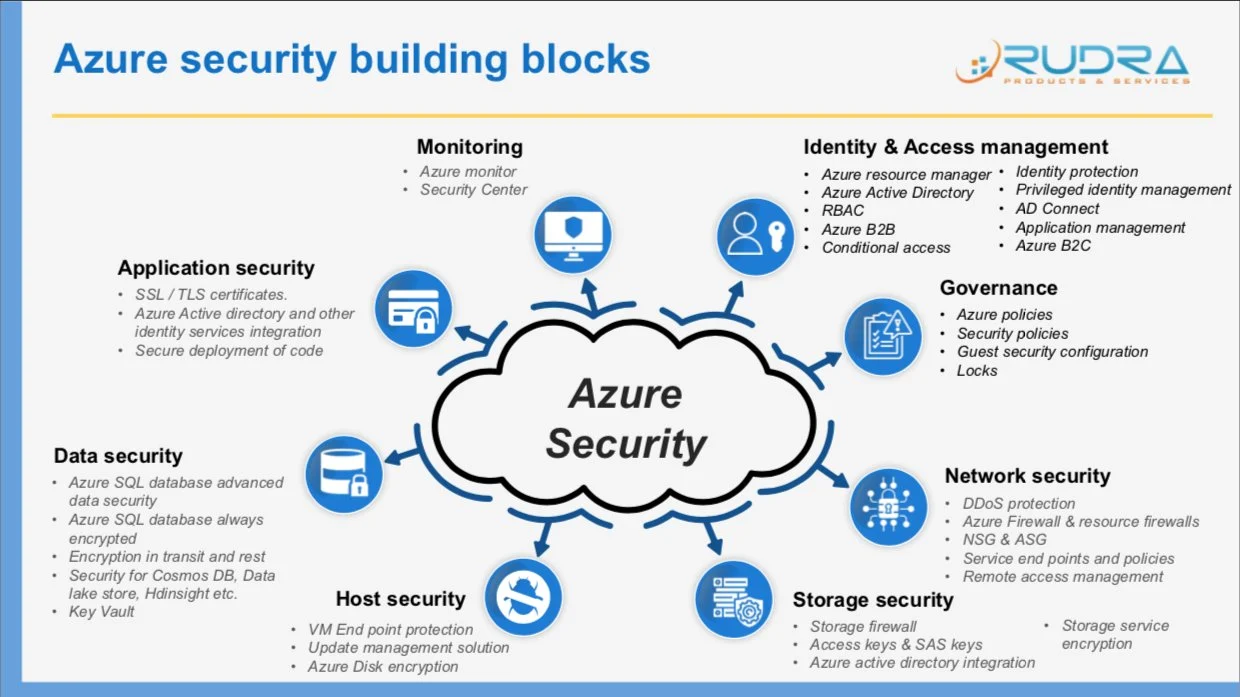
Azure Security Tools and Services
Azure provides a wide range of security tools and services to help you protect your cloud environment and assets effectively.
Azure Security Center
Azure Security Center is a unified security management and monitoring service that provides a centralized dashboard for managing security policies, assessing the security of your resources, and monitoring for potential threats. It helps you prevent, detect, and respond to security threats in your Azure environment.
Azure Sentinel
Azure Sentinel is a cloud-native security information and event management (SIEM) service that provides intelligent security analytics and threat intelligence across your entire environment. By using advanced machine learning algorithms, it helps you detect and respond to security incidents more efficiently and effectively.
Azure Information Protection (AIP)
Azure Information Protection (AIP) is a cloud-based solution that helps you classify, label, and protect your sensitive information. It allows you to define policies to automatically classify and protect sensitive data, control access to sensitive information, and track its usage. By using AIP, you can ensure that your sensitive data is protected and compliant with industry and regulatory requirements.
Best Practices for Azure Security and Compliance
In addition to the tools and services provided by Azure, there are several best practices you can follow to enhance the security and compliance of your Azure environment.
Regularly update and patch systems
Regularly updating and patching your systems is crucial in maintaining the security of your Azure environment. This includes keeping your operating systems, applications, and firmware up to date with the latest security patches and updates. By regularly updating and patching your systems, you can address known security vulnerabilities and protect against potential attacks.
Implement strong password policies
Implementing strong password policies is essential in preventing unauthorized access to your Azure resources. This includes enforcing password complexity requirements, setting password expiration policies, and implementing multi-factor authentication (MFA). By implementing strong password policies, you can significantly reduce the risk of password-related security breaches.
Regularly monitor and audit access logs
Regularly monitoring and auditing access logs is crucial in detecting and responding to potential security incidents. This involves monitoring for suspicious activities, analyzing access logs, and implementing an effective log management and retention strategy. By regularly monitoring and auditing access logs, you can detect potential threats and unauthorized access attempts early and respond to them effectively.
By following these best practices and utilizing the various tools and services provided by Azure, you can ensure the security and compliance of your cloud environment. By implementing strong access controls, enforcing network security, and encrypting your data, you can protect your cloud assets from potential threats and unauthorized access. By following secure DevOps practices, implementing continuous monitoring and testing, and having a well-defined incident response plan, you can respond to potential security incidents more effectively. With Azure’s comprehensive suite of security tools and services, you can enhance the security of your cloud environment and ensure the protection of your valuable assets.
