In our article, “GCP IAM Best Practices: Securing Access and Managing Permissions,” we explore the crucial topic of securing access and managing permissions within Google Cloud Platform’s Identity and Access Management (IAM) system. As businesses increasingly rely on cloud-based solutions, ensuring the proper level of security and permission management becomes paramount. We delve into this important aspect by discussing best practices for leveraging GCP IAM effectively and mitigating potential security risks. By implementing these best practices, organizations can safeguard their data and applications while granting appropriate access privileges to users.
Introduction to GCP IAM
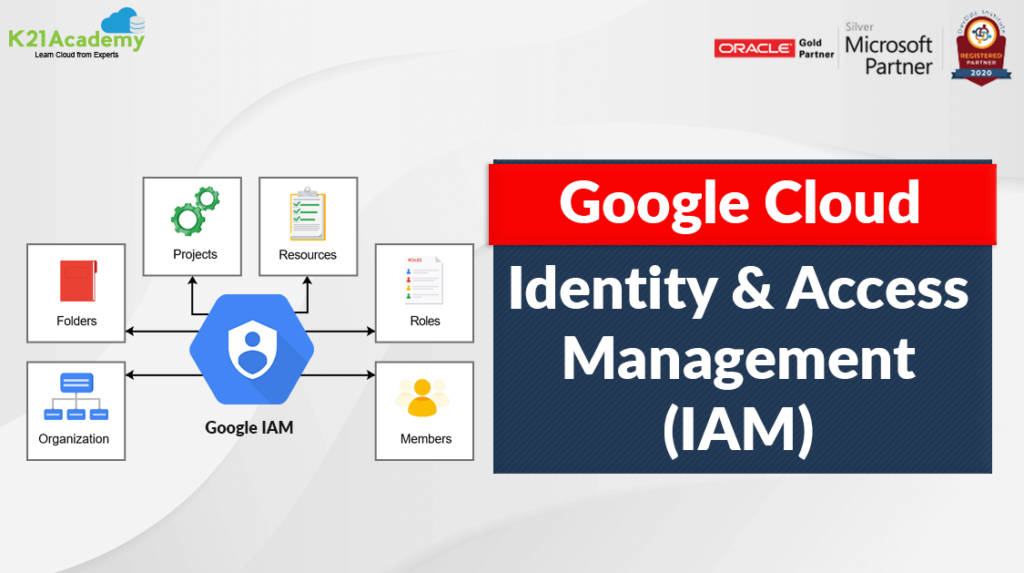
What is GCP IAM?
Google Cloud Platform Identity and Access Management (GCP IAM) is a comprehensive and powerful system that allows you to manage access to resources in your Google Cloud environment. IAM provides the foundation for controlling permission and ensuring the security of your organization’s data and services within GCP.
Why is IAM important for security?
IAM plays a critical role in securing your Google Cloud infrastructure and resources. By effectively managing access and permissions, you can prevent unauthorized users from accessing sensitive data, limit potential damage caused by insider threats, and ensure compliance with industry regulations. IAM helps you implement the principle of least privilege, ensuring that users are granted only the necessary level of access required to perform their specific tasks.
Key concepts and terminology
Before diving into the details of IAM, it’s important to familiarize ourselves with some key concepts and terminology.
-
Identity: An identity represents a user or entity that can request access to resources in GCP. This can include individual users, groups, or service accounts.
-
Role: A role is a collection of permissions that can be assigned to an identity. Roles define what actions users can perform on GCP resources.
-
Permission: A permission specifies an action that can be performed on a resource. Examples include read, write, create, or delete.
-
Service Account: A service account is a special type of account that represents an application or service rather than an individual user. Service accounts are commonly used when running applications or services within GCP.
These concepts form the foundation of IAM and help us understand how access control is managed within the GCP environment.
Understanding IAM Roles
Overview of IAM roles
IAM roles are a fundamental part of GCP IAM and are used to control access to resources. Roles define the permissions that are granted to users, groups, or service accounts. GCP provides a wide range of predefined roles that cover common use cases.
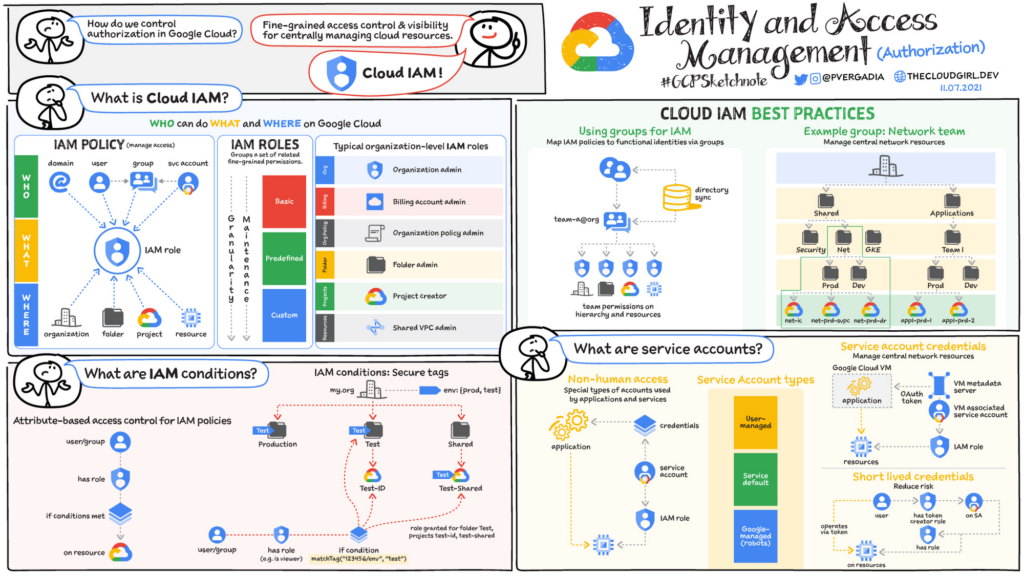
Predefined roles vs. custom roles
GCP offers a variety of predefined roles that are tailored for specific job functions, such as “Owner,” “Editor,” and “Viewer.” These predefined roles come with a set of permissions that are commonly needed for each role. However, in some cases, predefined roles might not meet your specific requirements. That’s where custom roles come in. Custom roles allow you to define fine-grained permissions that align with the specific needs of your organization.
Best practices for role assignment
When assigning roles in IAM, it’s important to follow best practices to ensure the security and efficiency of your GCP environment. Some key best practices include:
-
Least privilege: Grant users the minimum level of access required to perform their tasks. Avoid unnecessary or excessive permissions.
-
Role hierarchy: Establish a clear role hierarchy to avoid role duplication and make role management more manageable. This helps ensure that users have appropriate access without unnecessary complexity.
-
Regular reviews: Perform regular reviews of IAM roles and permissions to identify any unnecessary or outdated assignments. This helps minimize the risk of unauthorized access.
By following these best practices, you can effectively control access and reduce the risk of unauthorized access to your resources.
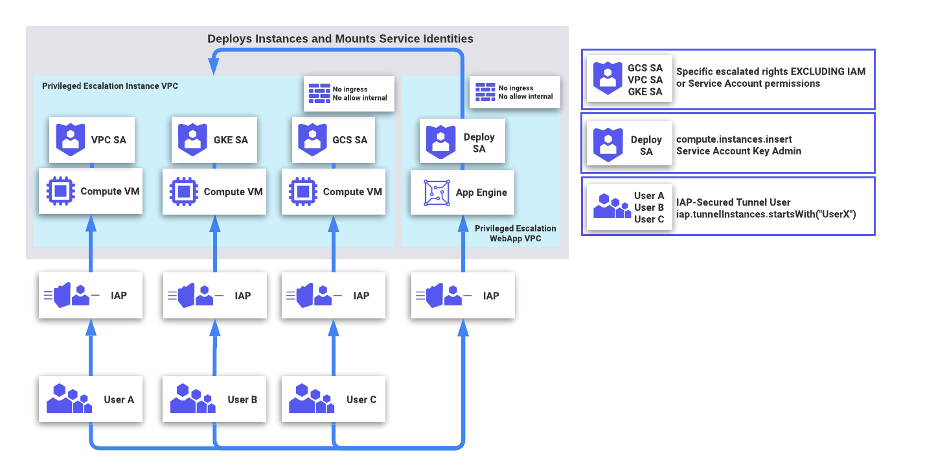
Creating and Managing Service Accounts
What are service accounts?
Service accounts are a key component of GCP IAM and are used to authenticate applications or services running within the Google Cloud environment. Unlike user accounts, service accounts represent applications rather than individual users. Service accounts can be assigned roles to determine the level of access they have to various resources.
Best practices for service account creation
When creating service accounts in GCP IAM, there are some best practices to keep in mind:
-
Separation of duties: Use different service accounts for different applications or services to enforce separation of duties. This helps minimize the impact of potential breaches or misconfigurations.
-
Limited scope: Grant service accounts only the necessary level of access required for their specific tasks. Avoid granting overly broad permissions that may increase the risk of unauthorized access.
-
Regular reviews: Regularly review the permissions assigned to service accounts to ensure they are still required and appropriate. Remove any unused or unnecessary permissions to minimize potential security risks.
By following these best practices, you can effectively manage your service accounts and maintain a secure Google Cloud environment.
Securing service account keys
Service account keys are credentials that allow an application or service to authenticate itself and access resources within GCP. It is crucial to secure these keys to prevent unauthorized access. Some best practices for securing service account keys include:
-
Key rotation: Regularly rotate your service account keys to minimize the risk of compromised keys. This helps ensure that any potential breaches are limited in their impact.
-
Key storage: Store service account keys securely, such as in a secure key management system or a secure credential storage solution. Avoid storing keys in code repositories or insecure locations.
-
Principle of least privilege: Grant service accounts only the necessary level of permissions required to perform their specific tasks. Avoid granting overly broad permissions that may increase the risk of unauthorized access.
By following these best practices, you can enhance the security of your service account keys and reduce the risk of unauthorized access to your Google Cloud resources.
Implementing Policies for Resource-level Access Control
Understanding resource-level access control
Resource-level access control allows you to define fine-grained permissions for individual resources within GCP. With IAM policies, you can control who can access specific resources and what actions they can perform on those resources. This helps you implement a strong security posture by granting access only to authorized users or entities.
Using Cloud Identity and Access Management policies
IAM policies in GCP are managed through Cloud Identity and Access Management (Cloud IAM). Cloud IAM allows you to create, update, and manage IAM policies for your Google Cloud resources. IAM policies are attached to resources and define who has what level of access to those resources.
Managing access control lists (ACLs)
Access Control Lists (ACLs) are another way to control resource-level access within GCP. ACLs allow you to specify granular permissions for individual resources, such as buckets or objects in Cloud Storage. By defining the list of authorized users or groups and their permissions, you can ensure that only authorized entities can access or modify specific resources.
When implementing resource-level access control, it’s important to carefully define and manage IAM policies and ACLs to prevent unauthorized access and maintain a secure GCP environment.
Enforcing Strong Password Policies
Importance of strong passwords
Passwords play a critical role in securing user accounts and preventing unauthorized access. Enforcing strong password policies helps protect against brute-force attacks and enhances the overall security of your GCP environment. By encouraging users to create complex passwords, you can significantly reduce the risk of compromised accounts.
Implementing password complexity requirements
To enforce strong password policies in GCP, you can leverage several features and settings:
-
Password length: Set a minimum password length requirement to ensure that passwords are not easily guessable.
-
Password complexity: Require the use of a combination of uppercase and lowercase letters, numbers, and special characters. This helps increase the entropy of passwords and makes them harder to crack.
-
Password expiration: Implement password expiration policies to regularly prompt users to change their passwords. This helps mitigate the risk of compromised passwords.
By implementing these password complexity requirements, you can help ensure that user accounts within your GCP environment are better protected against unauthorized access.
Enabling multi-factor authentication (MFA)
Multi-factor authentication (MFA) provides an additional layer of security by requiring users to provide two or more forms of authentication. By enabling MFA for GCP accounts, even if the password is compromised, an attacker would still need the additional factor, such as a physical token or a mobile app, to gain access. This significantly enhances the security of user accounts and prevents unauthorized access.
Enabling MFA is a highly recommended security enhancement that adds an extra layer of protection to your GCP environment.
Monitoring and Auditing IAM Actions
Overview of IAM audit logs
IAM audit logs provide a detailed record of various actions performed within your GCP environment. By monitoring and analyzing these logs, you can identify potential security issues, detect suspicious activities, and maintain a strong security posture.
Best practices for IAM log monitoring
To effectively monitor IAM actions, follow these best practices:
-
Enable IAM audit logs: Ensure that IAM audit logs are enabled for all relevant projects within your GCP environment. This ensures that comprehensive logs are available for monitoring and analysis.
-
Centralized log management: Aggregate IAM audit logs into a centralized logging solution, such as Stackdriver Logging. This allows for easier analysis and correlation of log data.
-
Automated log analysis: Leverage automated log analysis tools and techniques to detect anomalies, suspicious activities, and potential security incidents. This helps identify and respond to security threats in a timely manner.
By implementing these best practices, you can effectively monitor IAM actions and enhance the security of your GCP environment.
Using Stackdriver Logging and Cloud Pub/Sub for IAM notifications
Stackdriver Logging provides a powerful platform for collecting, analyzing, and visualizing log data. By leveraging Stackdriver Logging, you can centralize your IAM audit logs and perform real-time log analysis. Additionally, you can use Cloud Pub/Sub to generate notifications based on specific log events, allowing you to take immediate action in response to security incidents.
By combining Stackdriver Logging and Cloud Pub/Sub, you can enhance your IAM log monitoring capabilities and improve your incident response processes.
Managing Permissions with Google Groups
Introduction to Google Groups
Google Groups is a powerful feature within GCP IAM that allows you to manage permissions at scale. Groups make it easier to manage permissions for multiple users or service accounts by granting access to a group rather than individual entities.
Using groups for easier permission management
By utilizing Google Groups, you can simplify the process of managing permissions within your GCP environment. Instead of assigning permissions individually to each user or service account, you can assign permissions to a group and add or remove members as needed. This saves time and effort when granting or revoking access.
Best practices for managing group memberships
To effectively manage group memberships, follow these best practices:
-
Naming conventions: Use meaningful and descriptive names for your groups to easily identify their purpose and membership.
-
Role-based groups: Create groups based on specific job roles or responsibilities. This allows for easier management of permissions and ensures that users are assigned the appropriate level of access.
-
Regular audits: Regularly review group memberships and access permissions to ensure they align with current job roles and responsibilities. Remove any unnecessary or outdated memberships to maintain a secure and efficient GCP environment.
By adopting these best practices, you can leverage the power of Google Groups and simplify the management of permissions within your GCP environment.
Implementing IAM in Multi-project Environments
Challenges of managing IAM roles across projects
In multi-project environments, managing IAM roles and permissions can become a complex task. As the number of projects grows, it becomes increasingly challenging to ensure consistent access control and maintain a centralized view of permissions.
Best practices for cross-project IAM configuration
To effectively manage IAM roles across projects, consider the following best practices:
-
Organizational level configuration: Leverage Google Cloud Organizations to manage IAM roles and permissions at the organizational level. This allows for centralized management and consistent access control across projects.
-
Role hierarchies: Establish a clear role hierarchy that spans across projects. This helps maintain consistency and simplifies role management.
-
Regular reviews: Regularly review IAM roles and permissions across projects to identify any inconsistencies or outdated assignments. This helps minimize the risk of unauthorized access and improves the overall security of your multi-project environment.
By following these best practices, you can effectively manage IAM roles and permissions in multi-project environments and maintain a secure and streamlined access control strategy.
Using Google Cloud Organizations for centralized IAM management
Google Cloud Organizations provide a powerful solution for managing IAM roles and permissions across projects. By configuring IAM at the organizational level, you can ensure consistent access control and simplify the management of roles and permissions. Google Cloud Organizations also provide a centralized view of IAM policies, making it easier to monitor and review access controls.
By leveraging Google Cloud Organizations, you can effectively manage IAM in multi-project environments and ensure a streamlined and secure access control strategy across your GCP environment.
Securing IAM Policies with Conditions and Constraints
Understanding IAM policy conditions
IAM policy conditions allow you to define additional criteria that must be met for a permission to be granted. By using conditions, you can implement fine-grained access control based on various factors, such as the user’s IP address, time of day, or even specific attributes of the resource being accessed.
Implementing custom conditions for fine-grained access control
To implement custom conditions for fine-grained access control, consider the following:
-
Define the condition: Determine the specific criteria that need to be met for the permission to be granted. This can include factors such as network location, device type, or time of day.
-
Write the condition expression: Use the IAM condition expression language to define the condition as part of the IAM policy. This language allows you to express complex conditions based on various attributes and values.
-
Test and validate: Test the custom condition to ensure it functions as expected and grants access only to the intended users or entities. Validate the results to ensure that the desired access control is achieved.
By implementing custom conditions, you can enhance the granularity of your IAM policies and implement access control based on specific contextual factors.
Using policy constraints to enforce security policies
Policy constraints in IAM allow you to enforce security policies that apply across your GCP environment. Constraints define requirements that must be met for IAM policies to be valid. Examples of policy constraints include restricting resource locations or denying permission grants that violate specific policies.
By utilizing policy constraints, you can enforce security policies and ensure that access controls align with your organization’s security requirements and compliance standards.
Continuously Reviewing and Updating IAM Configurations
Performing regular IAM access reviews
Regularly reviewing IAM configurations is essential to maintaining a secure and efficient GCP environment. By conducting access reviews, you can identify any unnecessary or excessive permissions that might have been granted over time. This helps reduce the risk of unauthorized access and ensures that users only have the necessary level of access required to perform their tasks.
Identifying and revoking unnecessary permissions
During access reviews, it’s important to closely examine the permissions assigned to users, groups, and service accounts. Identify any permissions that are no longer required or exceed the scope of the user’s responsibilities. By revoking unnecessary permissions, you can reduce the attack surface and limit the potential impact of security breaches or insider threats.
Using IAM Recommender for configuration optimization
IAM Recommender is a powerful tool within GCP that provides recommendations for optimizing your IAM configurations. By analyzing the usage patterns of IAM roles and permissions, IAM Recommender can suggest changes to align access controls with the actual needs of your users.
By leveraging IAM Recommender, you can continuously optimize your IAM configurations and ensure that access controls remain efficient, secure, and aligned with the evolving requirements of your organization.
Conclusion
GCP IAM is a crucial component of securing your Google Cloud environment. By following best practices for IAM roles, service account management, resource-level access control, password policies, monitoring and auditing, group management, multi-project environments, policy conditions and constraints, and continuously reviewing and updating IAM configurations, you can maintain a secure and efficient access control strategy within your Google Cloud environment. By implementing these best practices, you can ensure that only authorized users and entities have access to your valuable resources while minimizing the risk of security breaches and unauthorized access.

