In the ever-evolving landscape of cloud computing, ensuring the security of our valuable assets has become paramount. With Google Cloud Platform (GCP) being a major player in the industry, it is crucial for us to adopt the best security practices available to protect our cloud assets. In this article, we will explore 10 GCP security best practices that will equip us with the necessary tools and knowledge to safeguard our valuable data and maintain the integrity of our cloud infrastructure. From authentication and access control to encryption and monitoring, these practices will enable us to confidently navigate the world of cloud security and protect our assets from potential threats.

1. Implementing Identity and Access Management (IAM)
In order to safeguard our cloud assets, one of the first and most crucial steps is to implement strong identity and access management (IAM) practices. This ensures that only authorized individuals or systems have access to our resources and data. Within IAM, there are several key principles and practices that we should follow:
1.1 Least Privilege Principle
The least privilege principle is a fundamental concept in IAM that ensures users are given only the permissions they need to perform their job responsibilities and nothing more. By granting users the least privilege necessary, we minimize the risk of unintentional or malicious access to sensitive information or actions. This principle helps to limit potential damage in the event that a user’s credentials are compromised.
To implement the least privilege principle effectively, we should regularly review user roles and permissions to ensure they align with current job requirements. This includes removing unnecessary access privileges and granting additional permissions only when absolutely necessary. Regular audits and monitoring of access logs can help identify any unauthorized access attempts or suspicious activity.
1.2 Service Accounts Management
Service accounts are special types of accounts that are used by applications or virtual machines to access other resources within the Google Cloud Platform (GCP). It is important to carefully manage and secure these service accounts to prevent unauthorized access and potential misuse.
To enhance the security of service accounts, we should follow these best practices:
- Regularly review and rotate service account keys to limit the risk of compromise.
- Never grant more permissions to service accounts than necessary.
- Monitor service accounts for any abnormal behavior or activity.
- Enable audit logging for service account activities to track any unauthorized access attempts or actions.
1.3 Identity Policy Management
Effective management of identity policies is crucial for maintaining a secure environment. Identity policies determine who can access specific resources and what actions are allowed within GCP. Here are some key considerations for identity policy management:
- Clearly define and document identity policies based on job roles and responsibilities within the organization.
- Regularly review and update identity policies to reflect any changes in job roles or organizational structure.
- Implement multi-factor authentication (MFA) for all user accounts to provide an additional layer of security.
- Monitor and enforce compliance with identity policies through regular audits and access reviews.
By implementing robust IAM practices, we can significantly reduce the risk of unauthorized access and better protect our cloud assets.
2. Network Security
Network security is a critical aspect of protecting our cloud assets. GCP offers various tools and features to help secure our Virtual Private Cloud (VPC) and ensure that network traffic is properly controlled and monitored.
2.1 Secure Your Virtual Private Cloud (VPC)
Creating a secure VPC is the foundation of network security in GCP. By default, resources within a VPC are isolated from external networks, providing an additional layer of protection. However, there are several best practices to follow when configuring and managing your VPC:
- Use private IP addresses for instances deployed within the VPC to prevent direct exposure to the internet.
- Utilize subnetting to segment the network and enforce stricter access controls.
- Implement network firewall rules to control incoming and outgoing traffic.
- Regularly review and update firewall rules to ensure they align with current security requirements.
2.2 Firewall Rules and Network Segmentation
Firewall rules are essential for controlling network traffic within our VPC. By defining the appropriate rules, we can allow or block specific types of traffic based on source IP addresses, protocols, and ports. Ensuring proper network segmentation is crucial for limiting potential attack vectors and preventing lateral movement within our environment.
To establish effective firewall rules and network segmentation, consider the following:
- Restrict access to only necessary ports and protocols.
- Use security groups to group resources with similar security requirements and apply consistent firewall rules.
- Implement secure connectivity solutions, such as Cloud VPN or Cloud Interconnect, for connecting on-premises networks to our VPC.
2.3 VPC Flow Logs
VPC flow logs provide valuable insights into network traffic within our VPC. By enabling VPC flow logs, we can capture and analyze network flows, including source and destination IP addresses, ports, protocols, and packet counts. These logs can be used for troubleshooting, monitoring, and detecting any suspicious network activity.
To make the most of VPC flow logs, consider the following best practices:
- Enable VPC flow logs for all subnets within our VPC.
- Integrate VPC flow logs with a logging and monitoring solution for real-time analysis and alerting.
- Regularly review and analyze flow logs to detect any potential security incidents or anomalies.
By implementing these network security best practices, we can strengthen our defenses and mitigate the risk of unauthorized network access and data breaches.

3. Data Protection
Protecting our data is of paramount importance when it comes to cloud security. GCP provides several features and services to help safeguard our data at rest and in transit.
3.1 Encryption at Rest
Encryption at rest ensures that data stored in GCP remains protected even if it is compromised or accessed without authorization. GCP offers several encryption options, including:
- Google-managed encryption keys: GCP automatically encrypts data at rest using Google-managed keys. These keys are protected by the highest security standards.
- Customer-supplied encryption keys (CSEK): With CSEK, we can manage and control the encryption keys used to encrypt our data. This gives us complete control over the encryption process.
- Cloud Key Management Service (KMS): Using KMS, we can manage and rotate encryption keys securely within GCP.
To effectively implement encryption at rest:
- Enable encryption at rest for all storage resources and databases.
- Regularly rotate encryption keys and review key management practices.
- Periodically audit and ensure compliance with encryption policies.
3.2 Encryption in Transit
Encryption in transit ensures that data transmitted between our resources and GCP services remains secure and protected from interception or tampering. GCP supports encryption in transit by default using industry-standard protocols such as TLS/SSL.
To ensure effective encryption in transit:
- Enable SSL/TLS for all web-based applications and services.
- Use the latest versions of encryption protocols to ensure strong security.
- Regularly update and patch cryptographic libraries and systems to mitigate potential vulnerabilities.
3.3 Data Loss Prevention (DLP)
Data loss prevention (DLP) mechanisms help prevent the accidental or intentional exposure of sensitive data. GCP offers data loss prevention features, including the Data Loss Prevention API, which can be used to scan and classify data for sensitive information.
To protect our data effectively, consider the following:
- Identify and classify sensitive data in accordance with organizational policies and regulatory requirements.
- Implement automated scanning and classification of data to detect and prevent data leaks or breaches.
- Regularly review and update DLP policies and detection rules to adapt to changing data protection needs.
By implementing strong data protection measures, including encryption and data loss prevention mechanisms, we can enhance the security of our sensitive data and prevent unauthorized access or exposure.
4. Incident Response and Monitoring
While prevention is important, it is equally important to be prepared for security incidents and to have effective incident response and monitoring strategies in place. GCP offers several tools and features to facilitate incident detection, response, and monitoring.
4.1 Security Incident Detection and Response
Implementing a robust incident detection and response framework is crucial for identifying and mitigating security incidents in a timely manner. GCP provides various tools and features to assist in this area, including:
- Cloud Security Command Center (Cloud SCC): Cloud SCC provides centralized visibility and control over our GCP resources. It enables us to detect and respond to security incidents quickly by providing insights and recommendations based on best practices and industry standards.
- Security Information and Event Management (SIEM) integration: Integrating GCP with a SIEM solution can enhance incident detection and response capabilities by aggregating and analyzing security events from various sources.
To effectively detect and respond to security incidents:
- Implement real-time monitoring and alerting systems for critical resources and access logs.
- Establish an incident response plan that includes roles, responsibilities, and steps to follow in the event of a security incident.
- Regularly test and update the incident response plan based on lessons learned and emerging threats.
4.2 Cloud Audit Logging
Cloud audit logging provides detailed logs of important activities and changes within our GCP resources. These logs can be used for auditing, compliance, and investigating security incidents. By enabling and analyzing audit logs, we can gain critical insights into potential security vulnerabilities or unauthorized activities.
To leverage cloud audit logging effectively:
- Enable audit logging for all GCP services and resources.
- Integrate audit logs with a centralized logging solution for real-time analysis and alerting.
- Regularly review and analyze audit logs to detect any potential security incidents or anomalies.
4.3 Cloud Security Command Center (Cloud SCC)
Cloud SCC offers a comprehensive view of security risks and vulnerabilities within our GCP environment. It provides centralized visibility, control, and guidance for security best practices. By using Cloud SCC, we can proactively identify and address security issues before they can be exploited.
To maximize the benefits of Cloud SCC:
- Regularly review the security dashboard of Cloud SCC to identify and prioritize potential security risks.
- Implement the recommended security best practices provided by Cloud SCC.
- Use the insights and recommendations provided by Cloud SCC to improve the overall security posture of our GCP environment.
By implementing effective incident response and monitoring strategies, we can detect and respond to security incidents promptly, minimizing potential damage and reducing the impact on our cloud assets.
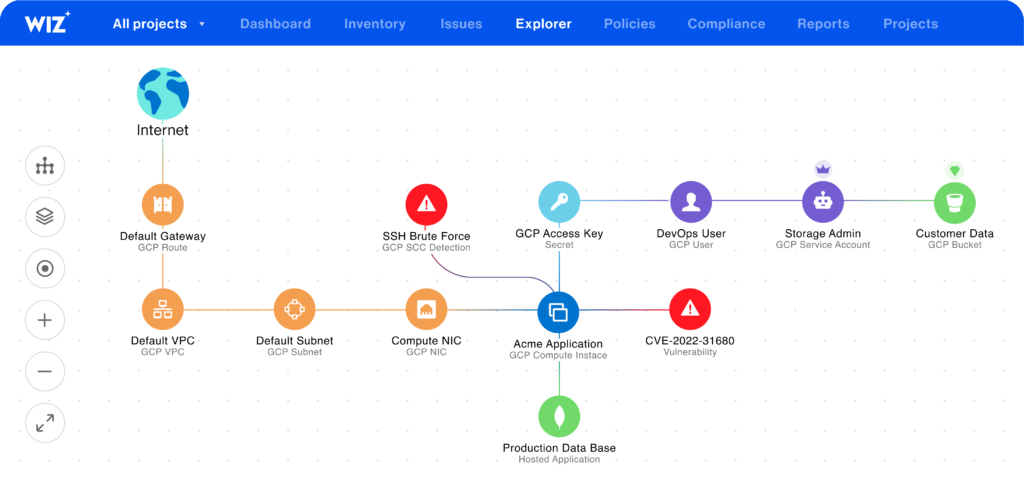
5. Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds an additional layer of security to the authentication process, requiring users to provide multiple pieces of evidence to prove their identity. GCP offers various MFA options that can be used to enhance the security of user accounts and protect against unauthorized access.
5.1 Enforcing MFA for User Accounts
Enforcing MFA for user accounts is an effective way to prevent unauthorized access to our GCP resources. By requiring users to provide an additional factor, such as a temporary code or biometric verification, we can significantly reduce the risk of unauthorized access even if passwords are compromised.
To enforce MFA for user accounts:
- Enable MFA for all user accounts within our GCP organization.
- Choose MFA methods that align with our security policies and user preferences.
- Encourage the use of hardware tokens or biometric authentication for added security.
5.2 Smart Card or Biometric Authentication
Smart card or biometric authentication methods can provide an additional layer of security by tying the authentication process to physical tokens or unique biological characteristics. These methods offer a more secure and tamper-proof means of verifying user identities.
To enhance security with smart card or biometric authentication:
- Integrate our identity provider or directory service with GCP to enable smart card or biometric authentication.
- Regularly review and update policies related to smart card or biometric authentication.
- Train users on the proper use and management of smart cards or biometric authentication methods.
5.3 MFA for Sensitive Operations
In addition to enforcing MFA for user accounts, it is crucial to require MFA for sensitive operations that can potentially cause significant harm if compromised. Granting additional protection to high-privileged accounts or critical operations can reduce the risk of unauthorized access or malicious actions.
To effectively implement MFA for sensitive operations:
- Identify and define sensitive operations within our GCP environment.
- Enforce MFA for all users performing sensitive operations.
- Regularly review and update the list of sensitive operations to reflect changing security requirements.
By implementing MFA for user accounts and sensitive operations, we can significantly enhance the security of our GCP environment and reduce the risk of unauthorized access and data breaches.
6. Secure Data Storage
Securing our data storage systems is crucial for ensuring the confidentiality, integrity, and availability of our data. GCP provides several features and services to help us secure our data storage systems effectively.
6.1 Cloud Storage Security
Cloud Storage provides secure and durable object storage that can be accessed from anywhere. To enhance the security of our Cloud Storage instances, we should follow these best practices:
- Use strong access controls and permissions to restrict access to our storage buckets.
- Encrypt data stored in Cloud Storage using Google-managed or customer-supplied encryption keys.
- Enable versioning for critical data to protect against accidental or malicious modifications or deletions.
- Regularly review access logs and audit logs to monitor and detect any unauthorized access attempts.
6.2 Cloud Key Management Service (KMS)
Cloud KMS is a managed service that allows us to create and control encryption keys used to protect our data in GCP. By using Cloud KMS, we can securely manage and rotate encryption keys, ensuring the confidentiality and integrity of our data.
To effectively utilize Cloud KMS:
- Centralize key management and avoid locally storing encryption keys.
- Implement key rotation policies to enhance security.
- Regularly audit and monitor key usage to identify any unauthorized access attempts.
6.3 Secrets Management
Secrets management involves securely storing and accessing sensitive information such as passwords, API keys, and credentials. GCP provides Secret Manager, a fully-managed secrets management service, to help us store and manage secrets in a secure manner.
To practice effective secrets management:
- Avoid hardcoding secrets within code or configuration files.
- Leverage Secret Manager to store sensitive information securely.
- Monitor and review access logs for Secret Manager to detect any unauthorized access attempts.
By implementing secure data storage practices, including encryption, key management, and secrets management, we can protect our data from unauthorized access or exposure.

7. Compute Engine Security
Compute Engine instances are the virtual machines within GCP that run our applications and services. It is crucial to secure these instances to prevent unauthorized access and potential compromise.
7.1 Secure Server Configuration
Configuring our servers securely is essential for protecting sensitive data and preventing unauthorized access. Here are some best practices for securing Compute Engine instances:
- Regularly update and patch the operating system and software running on our instances.
- Disable unnecessary services and ports to minimize potential attack vectors.
- Implement secure communication protocols, such as SSH or SSL/TLS, for remote access.
- Utilize hardened machine images or templates that adhere to security best practices.
7.2 Instance and OS Hardening
Instance and operating system (OS) hardening involves implementing additional security measures to further protect our Compute Engine instances. Some key considerations for instance and OS hardening include:
- Implementing secure network configurations and strict access controls, such as firewall rules.
- Enabling and configuring intrusion detection and prevention systems.
- Regularly monitoring and reviewing system and access logs for any signs of unauthorized access or suspicious activity.
- Applying security patches and updates promptly to address any potential vulnerabilities.
7.3 Secure Admin Access (SSH)
Secure Shell (SSH) is a widely used remote administration protocol for accessing Compute Engine instances. To ensure the security of SSH access:
- Disable SSH access using passwords and only allow key-based authentication.
- Regularly review and update SSH key pairs used for remote access.
- Leverage Identity-Aware Proxy (IAP) to provide secure, browser-based SSH access without exposing SSH ports.
By implementing compute engine security best practices, including secure server configuration, instance hardening, and secure admin access, we can greatly reduce the risk of unauthorized access and potential compromise of our Compute Engine instances.
8. Container Security
Containers are lightweight, isolated environments that package applications and their dependencies. When using containers within GCP, it is crucial to implement necessary security measures to protect against potential vulnerabilities and attacks.
8.1 Secure Container Images
Securing container images is essential for ensuring the integrity of our application code and preventing the execution of malicious or vulnerable code. Here are some best practices for securing container images within GCP:
- Only use trusted images from reputable sources or create our own images.
- Enable automated vulnerability scanning for container images to identify any known vulnerabilities.
- Regularly update and patch container images to incorporate the latest security fixes.
- Apply appropriate access controls to prevent unauthorized access to container images.
8.2 Container Vulnerability Scanning
Container vulnerability scanning helps us identify and remediate potential vulnerabilities within our containerized applications. GCP offers Container Analysis, a service that provides vulnerability scanning capabilities for container images.
To effectively use container vulnerability scanning:
- Integrate vulnerability scanning into our continuous integration/continuous deployment (CI/CD) pipeline.
- Act upon vulnerability findings by updating vulnerable dependencies or patching container images.
- Regularly review and update scanning policies based on emerging threats and changing security requirements.
8.3 Securing Container Runtime
Securing the container runtime environment is crucial to protect against potential attacks or compromises. Here are some best practices for securing the container runtime environment within GCP:
- Implement pod security policies to enforce container security requirements.
- Enable workload identity to provide secure access to GCP services from within containers.
- Monitor and analyze logs from container runtime to detect any potential security incidents or anomalies.
- Regularly review and update security policies and configurations for container runtime.
By implementing container security best practices, including securing container images, vulnerability scanning, and securing the container runtime, we can reduce the risk of vulnerabilities and better protect our containerized applications.
9. Resource Organizational and Management Best Practices
Organizing and managing resources effectively is essential for maintaining a secure and well-structured environment. By implementing resource management best practices, we can ensure proper access controls, effective monitoring, and efficient resource utilization.
9.1 Project and Resource Hierarchy
Properly organizing projects and resources within GCP is important for maintaining a clear and logical structure. Here are some best practices for project and resource hierarchy:
- Define a well-thought-out project and resource hierarchy that reflects our organization’s structure and security requirements.
- Implement resource-level access controls to limit access to specific projects or resources.
- Regularly review and update project and resource hierarchy to align with changing business needs.
9.2 Labels and Metadata
Labels and metadata provide a way to add more context and structure to our resources within GCP. By properly utilizing labels and metadata, we can enhance resource management, access controls, and monitoring. Here are some tips for labels and metadata:
- Apply consistent labeling conventions to resources for easier management and identification.
- Leverage labels for implementing granular access controls based on specific resource characteristics.
- Utilize metadata to provide additional information about resources, such as security classifications or compliance requirements.
9.3 Resource Monitoring and Cleanup
Proactive resource monitoring and regular cleanup of unused or unnecessary resources are essential for maintaining a secure and efficient environment. Here are some best practices for resource monitoring and cleanup:
- Implement centralized logging and monitoring to ensure visibility into resource activities and potential security incidents.
- Regularly review and analyze resource usage reports to optimize resource utilization and identify any anomalies.
- Establish a resource cleanup process to periodically identify and remove unused or unnecessary resources.
By following resource organizational and management best practices, we can improve resource visibility, access controls, and overall security and efficiency within our GCP environment.
10. Continuous Security Assessment and Compliance
Continuous security assessment and compliance are crucial for maintaining the security and integrity of our cloud assets. By regularly assessing our security posture and ensuring compliance with industry regulations and standards, we can identify potential vulnerabilities and ensure that our environment meets the necessary security requirements.
10.1 Regular Security Assessments
Regular security assessments, such as penetration testing and vulnerability scanning, can help identify potential security vulnerabilities and weaknesses within our GCP environment. Here are some best practices for conducting regular security assessments:
- Perform regular vulnerability scans to identify any known security vulnerabilities within our environment.
- Conduct periodic penetration testing to simulate real-world attacks and identify potential weaknesses.
- Review security assessment results and prioritize remediation actions based on severity and impact.
10.2 Compliance and Regulatory Standards
Compliance with industry regulations and standards is essential for ensuring the security and privacy of our data. GCP offers various compliance certifications and frameworks that we can leverage to demonstrate our commitment to security and compliance. Some key considerations for maintaining compliance within GCP include:
- Identify and understand the compliance requirements relevant to our organization, such as HIPAA or GDPR.
- Implement appropriate security controls and measures to meet compliance requirements.
- Regularly review and assess our environment for compliance gaps and remediate any identified issues promptly.
10.3 Security-by-Design Approach
Adopting a security-by-design approach ensures that security considerations are embedded into every stage of the development and deployment process. By taking a proactive approach to security, we can identify potential risks early on and implement controls to mitigate those risks.
To implement a security-by-design approach:
- Incorporate security requirements and controls into the development and deployment processes.
- Conduct security reviews and risk assessments throughout the development lifecycle.
- Provide security training and awareness programs to developers and other relevant stakeholders.
By continuously assessing our security posture, ensuring compliance with relevant standards, and adopting a security-by-design approach, we can ensure the ongoing security and protection of our cloud assets.
In conclusion, protecting our cloud assets within the Google Cloud Platform requires a comprehensive approach to security. By implementing strong identity and access management practices, securing our network, protecting our data, implementing incident response and monitoring strategies, enabling multi-factor authentication, and following best practices for secure data storage, compute engine security, container security, resource organizational and management, and continuous security assessment and compliance, we can safeguard our cloud assets and maintain a secure and resilient environment.